Vulnerability Scanning
Use Cases
Advanced technology meets expert analysis for comprehensive security assessment
Why Choose Our Vulnerability Scanning?
Advanced technology meets expert analysis for comprehensive security assessment
Proprietary Technology
Partner product scanning engine with cutting-edge detection capabilities
Detailed Reporting
Comprehensive, audit-ready reports with actionable remediation steps
Fast Results
Quick turnaround times without compromising on thoroughness
Risk Prioritization
Intelligent risk scoring to help you focus on critical vulnerabilities first
Our Scanning Process
A systematic approach to comprehensive vulnerability assessment
Scope Definition
We work with you to define the scanning scope, including systems, applications, and compliance requirements.
Automated Scanning
Our partner product IronVast scanner performs comprehensive automated vulnerability detection across your infrastructure.
Expert Analysis
Security experts validate findings, eliminate false positives, and provide context for each vulnerability.
Detailed Reporting
Receive comprehensive reports with risk ratings, remediation guidance, and compliance mapping.
See IronVast in Action
Comprehensive vulnerability management from target definition to detailed findings
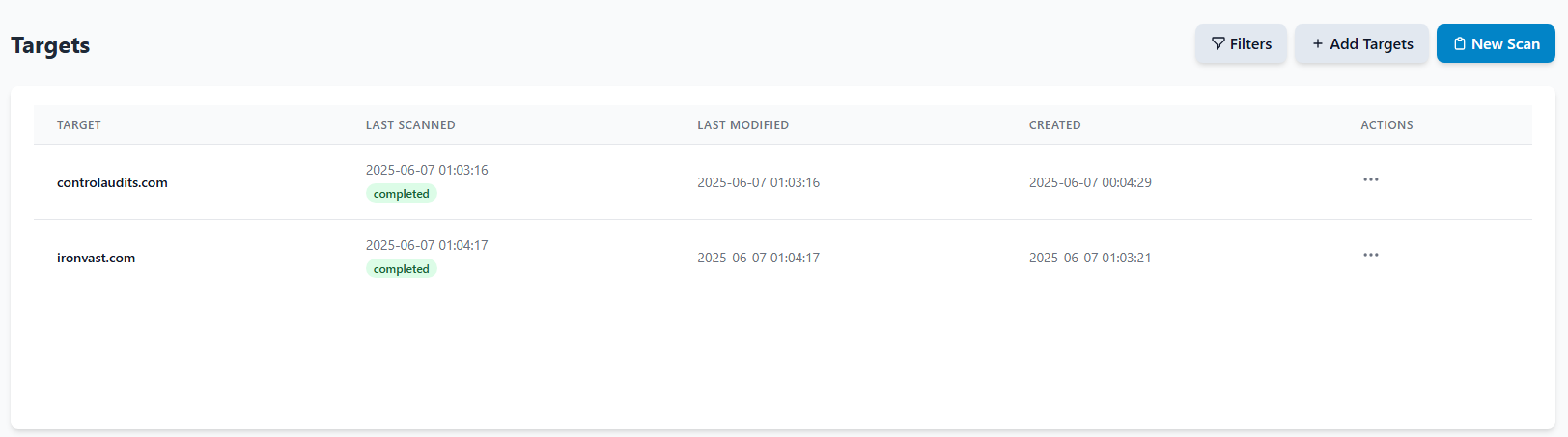
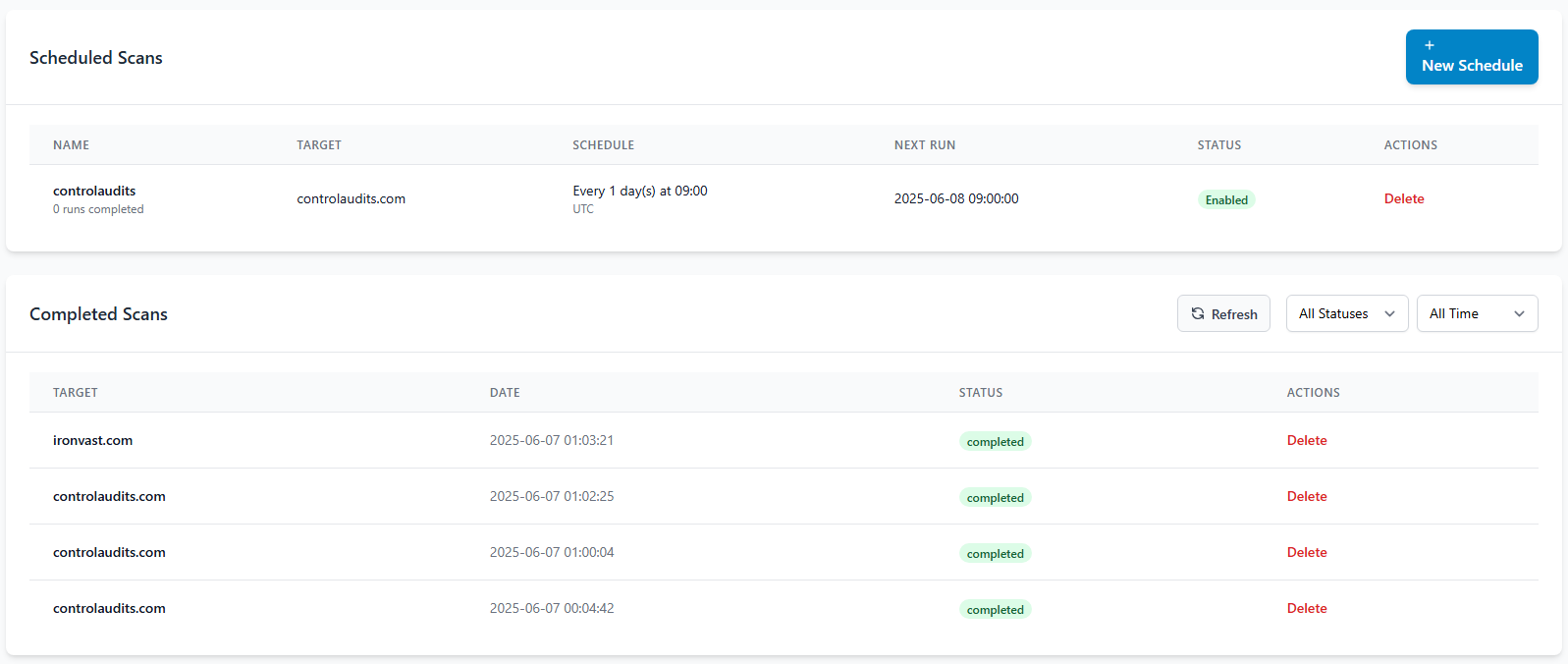
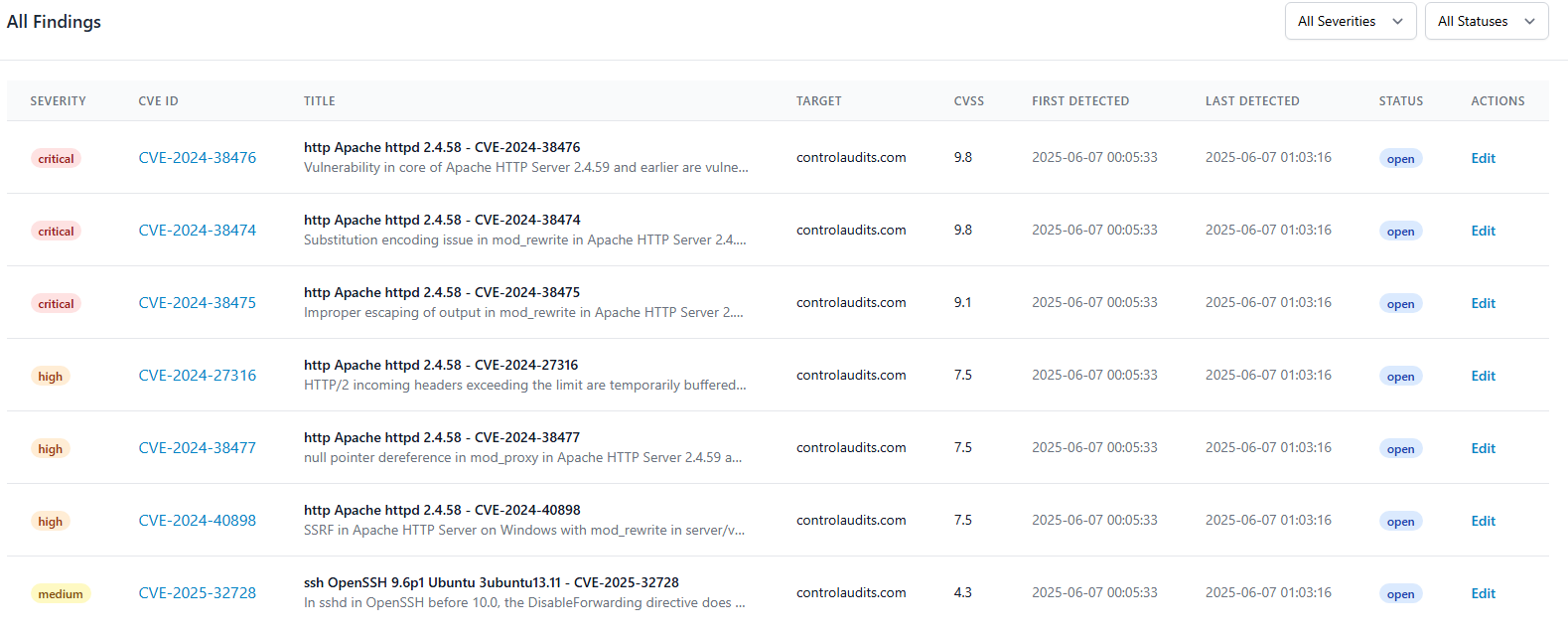
Target Management
Define and organize your scanning targets with comprehensive asset management capabilities.
Scan Execution
Monitor scan progress and schedule automated vulnerability assessments across your infrastructure.
Detailed Findings
Review comprehensive vulnerability reports with risk ratings and actionable remediation guidance.
Industry Use Cases
Tailored security solutions for every industry
Healthcare
HIPAA compliance, patient data protection, and medical device security assessment.
Financial Services
PCI DSS, SOX compliance, and financial data security for banking and fintech.
Government
Essential 8, AUS ISM compliance, and security clearance requirements for public sector.
Energy
AESCSF compliance and critical infrastructure protection for energy sector.
Education
ST4S compliance and student data protection for educational institutions.
E-commerce
Customer data protection, payment security, and online transaction safety.
Compliance & Standards
Our vulnerability scanning supports various compliance frameworks and industry standards
Ready to Secure Your Infrastructure?
For professional vulnerability scanning using our partner product IronVast, contact our security experts today.
